Enhanced Secure Thresholded Data Deduplication Scheme for Cloud Storage
| Venue | Category |
|---|---|
| TDSC'16 | Secure Deduplication |
Enhanced Secure Thresholded Data Deduplication Scheme for Cloud Storage1. SummaryMotivation of this paperEnhanced threshold-based deduplicated encryptionImplementation and Evaluation2. Strength (Contributions of the paper)3. Weakness (Limitations of the paper)4. Future Works
1. Summary
Motivation of this paper
Outsourced data may require different levels of protection, depending on how "popular" the datum is.
this differentiation based on popularity also can allevuates the user's need to mannually sort the data as common: deduplicated potentially sensitive (non-deduplicate)
Duplicate occurs only when the file becomes popular (i.e., shared by many users)
strictly confidential files that must never be deduplicated.
Enhanced threshold-based deduplicated encryption
- Target scenario the outsourced dataset contains few instances of some data items and many instances of others.
two backup types:
- uploaded by many users: benefit strongly from deduplication
- uploaded by one or very few users only: require confidentiality
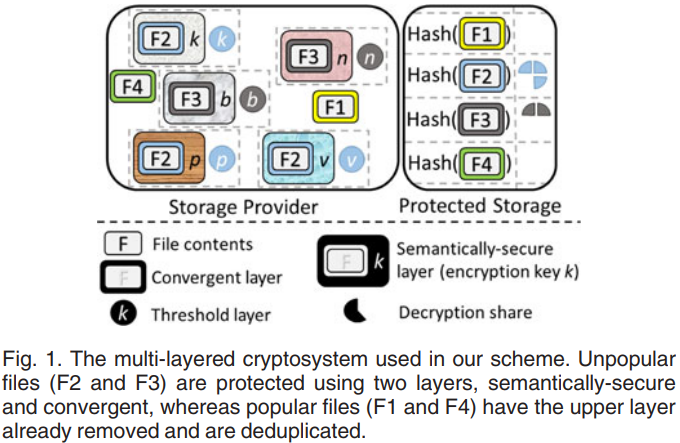
- Multi-layered cryptosystem
- the inner layer is applied using convergent encryption.
- the outer layer is applied using a semantically secure cryptosystem.
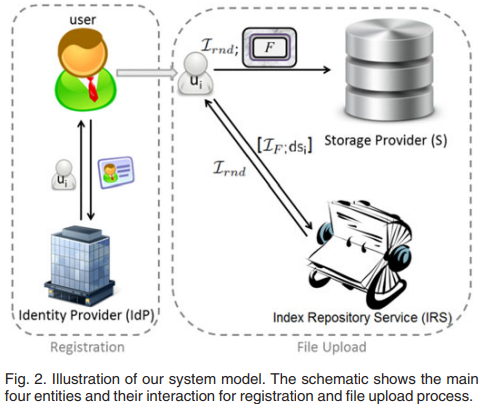
- System model Add two trusted entities: identity provider and index repository service.
- identity provider: users are identified when a user first joins the system.
- index repository service: generate the file identity.
- Security Model The method of this paper achieves two kinds of security notions:
- semantic security for unpopular data
- conventional convergent security for popular data prevent the storage provider which is honest-but-curious.
- Popularity definition
- a system-wide popularity limit Represents the smallest number of distinct, legitimate users that need to upload a given file for that file to be declared popular.
- A file shall be decleared popular When at least uploads for this file have taken place.
This paper just considers a single threshold .
Implementation and Evaluation
- Setting Dataset
- pirate bay dataset: each torrent represents a file (file popularity)
- Ubuntu popularity contest
- Compare with three related work Dupless, ClearBox, PAKE
- Storage space reducation This paper mentions the efficiency of its scheme depends on
- the value of (the tunable parameter of the scheme)
- the popularity distribution of files in the dataset
- Overhead
- Client computation
- Server computation
- Communication
- Dropbox interact
2. Strength (Contributions of the paper)
- This paper proposes an enhanced threshold cryptosystem that leverage popularity and allows fine-grained trade-off between security and storage efficiency
trade-off between security and storage efficiency
- This paper also disscuss the overall security of the proposed scheme
how to improve it?
3. Weakness (Limitations of the paper)
- In this paper's model, it needs to trust the identity provider (IdP) and Index Repository Service (IRS)
4. Future Works
- This paper mentions the case that how to prevent the attacker from guessing whether two ciphertexts produced by the same user corrspond to the same plaintext with a non-negligible advantage.
- The first dataset used in this paper can indicate the file popularity.
Pirate Bay dataset