How to Best Share a Big Secret
| Venue | Category |
|---|---|
| SYSTOR'18 | Secure Deduplication |
How to Best Share a Big Secret1. SummaryMotivation of this paperHow to best share a big secretImplementation and Evaluation2. Strength (Contributions of the paper)3. Weakness (Limitations of the paper)4. Some Insights (Future work)
1. Summary
Motivation of this paper
Motivation
Data-protection approaches are considered computationally expensive.
- data encryption and secret-sharing
This paper intends to present the first end-to-end comparison of state-of-art encryption-based and secret sharing data protection approaches.
previous evaluation results do not provide a clear picture of how these schemes compare in terms of application-perceived read and write throughput.
the combination of a random number generator, erasure code, and encryption algorithm
- determine which one becomes the bottleneck
How to best share a big secret
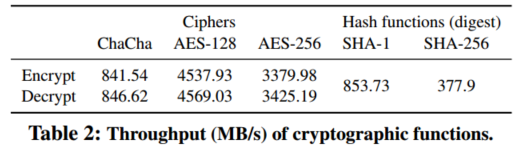
Encrypt files at the client side
Key-based encryption: (provide computational security)
encryption is considered computational expensive.
- require key generation and management
- hardware accelerators
Secret sharing: (cloud of clouds, provide information-theoretic security)
combines the user's original data with redundant random data
the original data can only be decoded by obtaining all of the encoded pieces.
Without requiring maintenance of encryption keys.
Drawback:
- generate a large amount of random data.
- incurs significant storage overhead
information-theoretic security vs. computational security
- information-theoretic security computational security
To eliminate two major bottlenecks of data protection
- Secure RAID: computational overhead is comparable to that of erasure coding.
- Hardware cryptographic libraries.
Evaluate all stages of the data path:
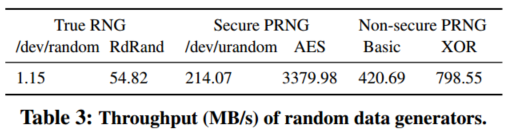
Random data generation
true random: external noise or hardware interrupts: /dev/random
- very slow
CSPRNG: whose seed must be generated by a true random generator: /dev/urandom
Encoding and encryption overheads
Overall throughput
Comparison
- Reed-Solomon (RS): only provide fault tolerance.
- Encryption: encrypt the data with a key-based symmetric cypher and encodes the result with RS.
- AONT-RS: hash the encrypted data, combines the result with the encryption key, and encodes the entire package with RS.
- Shamir's secret-sharingf scheme (SS): combine security and fault tolerance in non-systemic encoding
- Secure RAID: combine security and fault tolerance in two encoding rounds based on RS.
Computational overhead
- the low throughput of true random data generation precludes information-theoretical security in real system
- the performance of AONT-RS is limited by the crytographic hash
- secure RAID eliminates the computational bottleneck of secret sharing.
For End-To-End Evaluation
Aim: to understand the effect of the various system-level parameters on the bottlenecks.
- storage and network bandwidth
Setting: multi-cloud (EC2), a distributed object store prototype. re-implement all schemes in Java.
Once storage and network bottlenecks are introduced, secret-sharing is outperformed by encryption based techniques
- additional I/O and transfer overhead
- bottleneck shift
Implementation and Evaluation
2. Strength (Contributions of the paper)
- This work mentions information-theoretical security is infeasible in real system implementations
high cost of true random data generation.
- The bottleneck in real implementations shifts from
- computational complexity
- storage throughput (on local storage)
- network bandwidth (in cloud deployments)
- This paper also suggests that encrypting the data and dispersing the keys with an efficient secret sharing scheme is optimal for multi-cloud environments
3. Weakness (Limitations of the paper)
4. Some Insights (Future work)
- Security issue in cloud Majority of cloud service providers do not specify in their terms of service that data is owned by the customers, and lack security mechanisms to protect it.
data leakage from the cloud have been recently documented.
- drawback of the single cloud
vendor lock-in outage that a single cloud provider might suffer
- Data encryption AES: fixed-length string: 128 bits
AES-128: key size is 128 bits AES-256: key size is 256 bits